As in other years, the Security Intelligence Report offers an overview over the previous year’s security events and recommends ways to combat prevalent threats. Microsoft bases its report on analysis of cloud services and on-premises systems. Microsoft says it analyzed various sources covering 6.5 trillion security signals that pass through its cloud infrastructure each day. The company also collaborated with global security researchers to reach the following core conclusions:
Ransomware attacks are on the decline. Cryptocurrency mining is prevalent. Software supply chains are at risk. Phishing remains a preferred attack method.
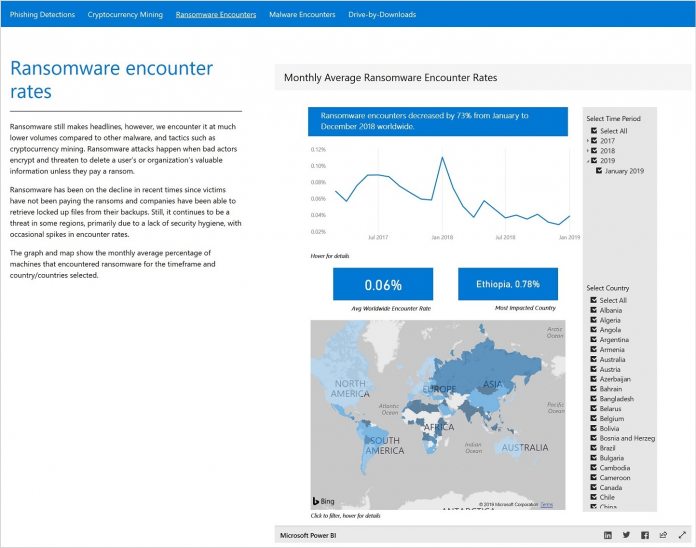
Throughout the last five years, ransomware attacks have become an increasingly dangerous attack method. However, in 2018, the number of overall ransomware attacks declined, a situation Microsoft describes as “notable”. The company says the data shows the security community is successfully pushing back against attackers and forcing them to change methods. “We believe that attackers have shifted from this highly visible method to more stealth attacks because users have gotten smarter about how they respond.” Elsewhere in the Security Intelligence Report, Microsoft says cryptocurrency mining is becoming more frequent. The company points out attackers are mining as a replacement for ransomware. Due to the huge computational needs to mining coins, attackers are circumnavigating by installing malware onto PCs and effectively stealing power to mine coins. Bad actors are also turning their attention to the software supply chain. One tactic the SIR notes is attackers placing a compromised component into an otherwise clean application. What makes these attacks worrisome is their ability to go largely undetected.
All About the Phish
While other areas concern Microsoft, the Security Intelligence Report shows phishing remains the preferred attack method. Due to its relative ease, the company expects phishing to remain the malware vector of choice for some time. “Attackers will continue to use and advance their social engineering techniques because of the success they’ve had with them. We see attackers using domain name spoofing – to impersonate emails to look like they’re coming from known brands or colleagues, and catchy subject lines as successful methods to get users to click open emails. Very targeted spear phishing has proven to be a successful approach, especially in business email compromise scams.”